Topics from Aarhus University
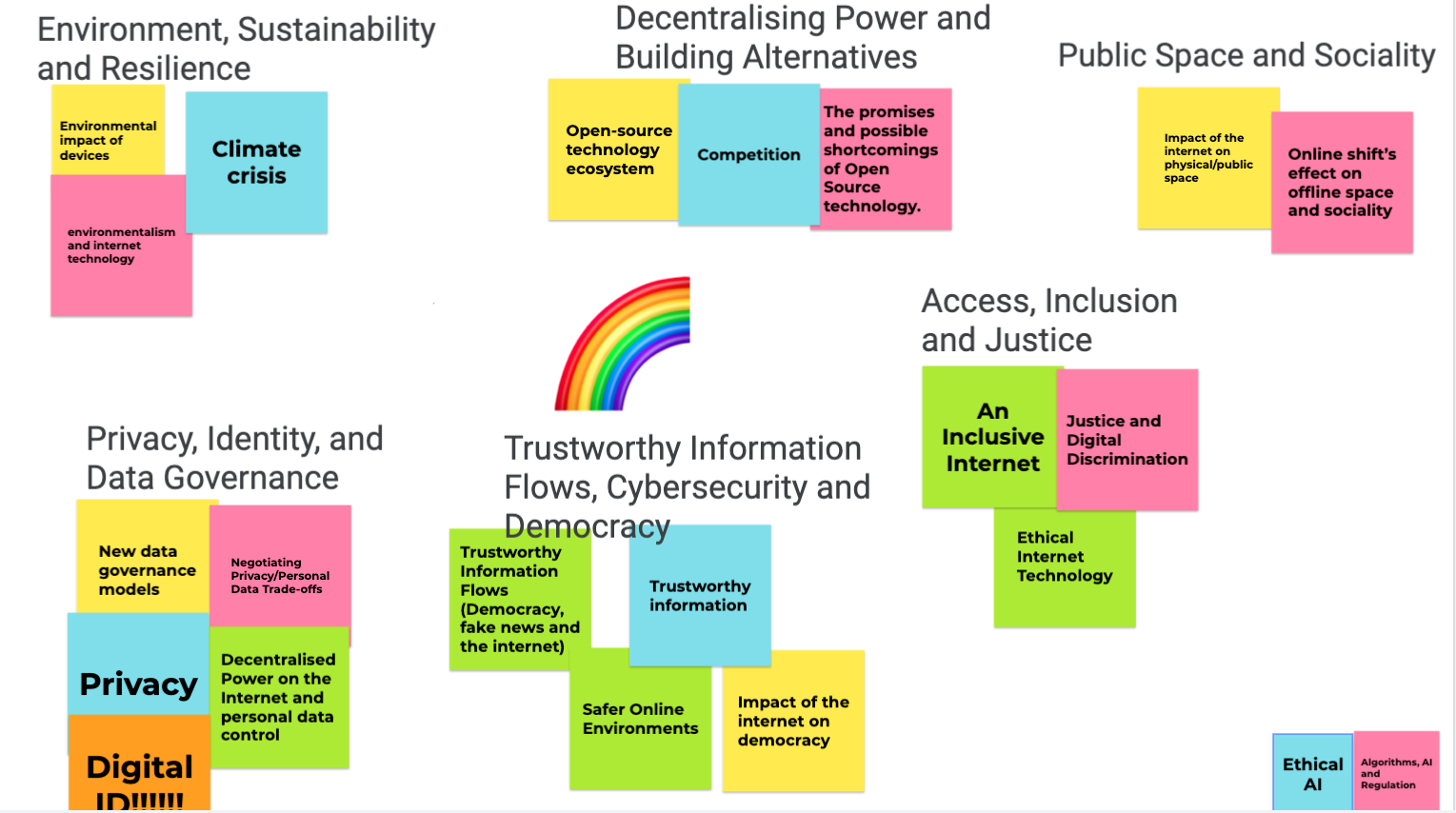
We have made a selection of topics based on last year’s D1.13, D.1.9 and the insights gathered through this year’s workshop. In order to select only 5 topics, we have looked at the overlap between the 8 NGI goals and the group discussion that came up during the workshop. This year, we had 6 different groups, and the prompt for discussion was to choose an example from the last two years in which human-centered values or democratic principles had been affected. Like this, the discussion was directed but not constrained according to previous results.
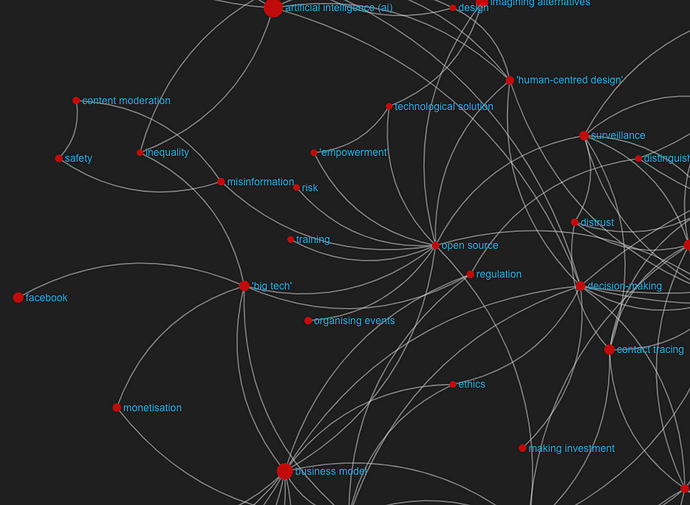
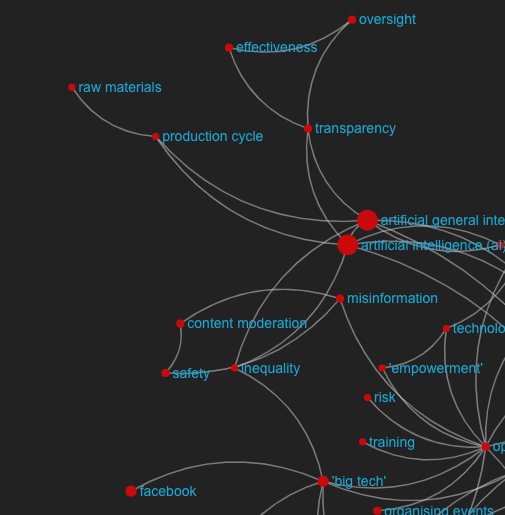
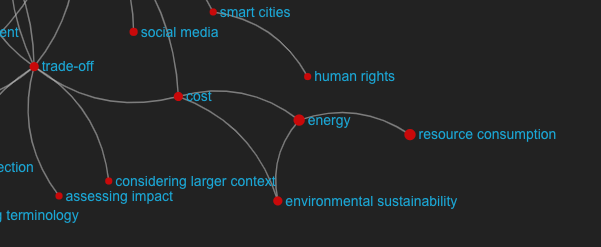
From the workshop D1.9
8 selected key topics:
● Trustworthy Information Flows
● Decentralised Power on the Internet
● Personal Data Control
● Sustainable and Climate-friendly Internet
● Safer Online Environments
● An Inclusive Internet
● Competitive European Ecosystems
● Ethical Internet Technology
1. Ethical Internet Technology
Last year, one of the 8 NGI goals arising from the analysis and the workshop was concerned ethical internet technology. This is quite a broad topic that came up again during this year’s workshop, reflected in different subtopics chosen by the different discussion groups (3 out of 6 groups). In particular, groups highlighted areas such as video surveillance, implementation of internet technology, and discrimination resulting from algorithmic decision-making as areas of high priority for the next years. Overall, we can take the motto ‘moving fast and breaking things’ as a reflection of the attitude that needs to be seriously reconsidered. Some of the policies and regulations that were proposed around these areas include correcting the data collection imbalance, increasing the diversity at the higher level of policy making, and including mandatory ethics education in technical studies (i.e., computer scientists, engineers, etc). In addition to focusing on diversity to decrease discrimination bias, special emphasis was placed on the importance of testing decision-making algorithms and setting up requirements for public debates and transparency before implementation.
Challenges discussed in the second workshop within this topic: Video surveillance (for decision-making), Implementing technology without proper discussions and transparency, Descriminating Algorithmic decision-making
Methods: output of workshop D1.14 and workshop D1.9. At workshop D1.14, we split the participants into 6 groups, where each could choose a topic for discussion. 3 of the 6 groups had a topic in this category. The topic was one of 8 selected topics of the workshop D1.9.
We think it is important, because: ethics is the fundament for identifying European values and solving social issues, which is one of the main objectives of the project (objective 2 in the grant agreement part B).
2. An Inclusive Internet
Last year, limited access to the internet was highlighted as one of the problematic areas, referring to half of the population still being offline, and urban areas being better connected than rural. Many disabled people also are excluded from using online information and services, so inclusive infrastructures and tools are needed to remove barriers and create an inclusive and accessible Internet for all. This year we saw this topic resurface in several of the discussions (2 out of 6 groups), in particular referring to the many internet shutdowns carried out by governments to suppress protests or movements in 2020. According to Human Rights Watch, this has occurred in Bangladesh, the Democratic Republic of Congo, Egypt, India, Indonesia, Iran, Iraq, Sudan Myanmar and Zimbabwe. Possible solutions suggested during the expert workshop included the development of international legislation and centralising the point of control to the international neutral level.
Challenges discussed in the second workshop within this topic: Unstable and no access to the internet, Shut down of internet by governments to suppress protests or movements.
Methods: output of workshop D1.14 and workshop D1.9. At workshop D1.14, we split the participants into 6 groups, where each could choose a topic for discussion. 2 of the 6 groups had a topic in this category and the topic came up in a third group as well. The topic was one of 8 selected topics of the workshop D1.9.
We think it is important, because: inclusivity is one of the European values mentioned in the grant agreement (Annex 1, p. 4).
3. Trustworthy Information Flows (Democracy, fake news and the internet)
It is widely recognised that trustworthy information flows are essential for healthy democracies, and this year’s covid crisis and the associated infodemic has given us a new perspective of the importance of reliable information. While the spread of disinformation did not arise as one of the preferred topics for discussion among the 6 groups, we asked explicitly about the best strategy to combat misinformation in a quiz to be completed at the individual level. There, the majority of responders chose the option referred to gaining a better understanding of why people share fake news (34.8%), followed by counteracting with accurate information (17.4%) and developing better fake news detection algorithms (8.7%). This further relates to other democracy threats mentioned above, governmental censorship and large-scale content moderation by online platforms.
Challenges discussed in the second workshop within this topic: Shut down of internet by governments to suppress protests or movements
Methods: output of workshop D1.14 and workshop D1.9. At workshop D1.14, we split the participants into 6 groups, where each could choose a topic for discussion. 1 of the 6 groups had a topic in this category. The topic was one of 8 selected topics of the workshop D1.9.
We think it is important, because: trustworthiness is one of the European values mentioned in the grant agreement (Annex 1, p. 4).
4. Decentralised Power on the Internet and personal data control
The internet of today is controlled by a handful of giant companies with virtual monopoly control, acting as gatekeepers by enforcing policies on their users. This is one of the 8 NGI topics from last year which resurfaced in this year’s workshop around recent data leaks. In particular, a leak of governmental health data in Finland, where data had been used to blackmail citizens, was used as an example to illustrate this issue. This ties in with personal data control, and solutions proposed evolved around ideas of more efficient data de-anonymisation, the establishment of a human rights to slow down personal data collection, and more accountability at different levels.
Challenges discussed in the second workshop within this topic: Risk of data leaks.
Methods: output of workshop D1.14 and workshop D1.9. At workshop D1.14, we split the participants into 6 groups, where each could choose a topic for discussion. 1 of the 6 groups had a topic in this category. The topic was one of 8 selected topics of the workshop D1.9.
We think it is important, because: decentralisation and promoting privacy are two of the European values mentioned in the grant agreement (Annex 1, p. 4).
5. Safer Online Environments
Cyberviolence and hate speech was also chosen this year as vital in order to build a safer and more human-centric online environment. For this to happen, a range of issues needs to be taken into consideration, including the role of social media providers and the protection of free expression. At the same time, solutions need to be investigated, such as effective moderation or containment procedures, creating useful aid for victims of cyberviolence and enabling law enforcement to take action against offenders.
Challenges discussed in the second workshop within this topic: How to protect minorities from discrimination and hate speech, and how to provide equal access
Methods: output of workshop D1.14 (?) and workshop D1.9. At workshop D1.14, we split the participants into 6 groups, where each could choose a topic for discussion. 1 of the 6 groups had a topic in this category. The topic was one of 8 selected topics of the workshop D1.9.
We think it is important, because: openness is one of the European values mentioned in the grant agreement (Annex 1, p. 4).